Encryption using Caesar's cipher
Overview
We’ll use the substitution cipher technique in this shot. In this technique, the text characters are replaced by other numbers, characters, or symbols. The substitution cipher technique is the earliest known cipher technique invented by Julius Caesar.
In this cipher technique, we replace each letter of the alphabet with a letter that is standing three places further:
- In the generalized version of Caesar’s cipher each alphabet is replaced with another alphabet after shifting it
xtimes to the right. - The amount of the
shift (x)is the encryption key. - For the decryption process, we reverse the process and replace the ciphertext alphabet with the alphabet after doing a
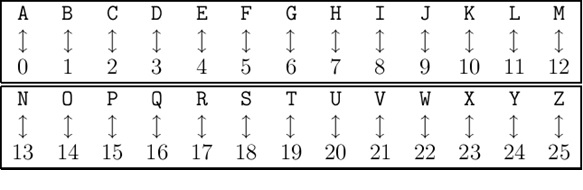
left shift by x alphabets. - The numerical equivalent to each letter is shown below:
Note:
- Encryption:
(PT+Key)mod26- Decryption:
(CT-Key)mod26
Let’s try to solve Caesar cipher with an example, assuming The given PT=CRYPTOLOGY and Key=3:
- C1=(2+3)mod 26 =5 that is
F - C2=(17+3)mod26= 20 that is
U - C3=(24+3)mod 26=1 that is
B - C4=(15+3)mod 26=18 that is
S - C5=(19+3)mod 26=22 that is
W - C6=(14+3)mod 26=17 that is
R - C7=(11+3)mod 26=14 that is
O - C8=(14+3)mod 26=17 that is
R - C9= (6+3)mod 26=9 that is
J - C10=(24+3)mod 26=1 that is
B
The ciphertext for
CRYPTOLOGYisFUBSWRORJB.
Limitations
- If it is known that the given ciphertext is Caesar cipher, then a brute-force cryptanalysis is easily performed.
- Since there are only 25 combinations to search out for given plaintext.
Implementation of Caesar’s cipher
#include<stdio.h>#include<string.h>int main() {char pt[50],ct[50];int key,i;//printf("Enter the palintext:");scanf("%s",pt);// printf("Enter the key:");scanf("%d",&key);for(i=0;i<strlen(pt);i++){if(pt[i]>=65 && pt[i]<=90){ct[i]=(((pt[i]-65)+key)%26)+65;}else if(pt[i]>=97 && pt[i]<=122){ct[i]=(((pt[i]-97)+key)%26)+97;}elsect[i]=pt[i];}ct[i]='\0';printf("Cipher Text is:");puts(ct);}
Enter the input below
Explanation
- Lines 4 to 5: We declare the variable for plain text and cipher key,key and looping variable
pt[50],ct[50];key, andi;. - Lines 6 to 9: We take user-defined input that is
Plain TextandKey. - Lines 10 to 22: We know that the plain text and ciphertext can be either capital or small letters so we use ASCII values for that and perform
(P+K)mod 26. - Lines 23 to 25: Whenever the plain text length exceeds we end the ciphertext with a null value by using
\0So, that we don’t encounter any garbage value. - Line 26: We print the corresponding ciphertext using
puts()in the end.